Hipaa Soc 2: A Practical Guide for Personal Injury Law Firms (hipaa soc 2)

For any modern personal injury firm, handling client data has moved far beyond a simple IT checklist—it's now a central part of your business strategy. The real challenge is making sense of complex compliance frameworks, especially HIPAA and SOC 2, which have become the two most critical standards for protecting sensitive information. For any firm using technology to manage Protected Health Information (PHI), getting a firm grasp on their distinct roles is non-negotiable.
Why Data Security Is a Strategic Imperative for PI Firms
In the high-stakes environment of personal injury law, data security is no longer just an expense. It's the bedrock of client trust and operational integrity. Your firm manages a massive amount of Protected Health Information (PHI) every single day, from detailed medical records and treatment plans to sensitive diagnoses and billing data. This information is essential to winning your cases, but it also makes you a prime target for cybercriminals.
A data breach is far more than a technical glitch. It's a catastrophic event that can lead to crippling financial penalties, destroy your firm's reputation, and completely shatter client confidence.

The Soaring Cost of Non-Compliance
The threat is more real today than ever before. In 2023, the U.S. Office for Civil Rights (OCR) reported 725 breaches that each affected 500 or more people, exposing the private records of an unbelievable 168 million individuals. It was a record-breaking year for both the number and the scale of breaches, highlighting a ruthless trend: hackers are targeting the healthcare sector with precision, with hacking incidents causing nearly 80% of these major data leaks.
For a personal injury firm, the fallout from a breach is immediate and severe:
- Financial Penalties: Fines for HIPAA violations are no small matter, ranging from thousands to millions of dollars depending on the degree of negligence.
- Reputational Damage: Once a breach goes public, the trust you've painstakingly built with clients can evaporate overnight, making it incredibly difficult to attract new cases.
- Operational Disruption: The process of responding to a breach consumes critical time and resources, pulling your team away from client work and bringing productivity to a standstill.
Introducing HIPAA and SOC 2
Two frameworks stand out as the primary defenses against these threats: HIPAA and SOC 2. While people often mention them in the same breath, they have different, though complementary, functions. HIPAA is a federal law that defines what you are required to protect (PHI) by setting specific rules for its privacy and security. SOC 2, on the other hand, is an auditing framework that evaluates how a service organization protects data, providing tangible proof of its internal controls.
Key Takeaway: It’s crucial to see compliance as a strategic investment, not just a line-item expense. A strong security posture, verified by frameworks like HIPAA and SOC 2, gives you a competitive edge and proves your unwavering commitment to protecting client data.
As PI firms increasingly rely on AI-powered tools to review medical records, understanding the relationship between HIPAA and SOC 2 is essential. It ensures you’re not only meeting your legal duties but also choosing vendors who are equally committed to the highest security standards. You can learn more about our enterprise-grade security practices at https://areslegal.ai/security and see how we safeguard your firm’s most sensitive information. This guide will demystify these frameworks to help you build a more resilient and trustworthy practice.
Decoding the Frameworks: A Primer on HIPAA and SOC 2
Before diving into compliance strategies, personal injury firms need a solid grasp of what HIPAA and SOC 2 are and, more importantly, what they aren't. While both frameworks are designed to protect sensitive information, they come from two completely different places. Think of it this way: HIPAA is the law—it tells you what you're legally required to protect. SOC 2, on the other hand, is a voluntary audit that proves how well you protect it.
For a legal team juggling massive amounts of client data, understanding this difference isn't just a technical exercise. It’s a strategic one that directly impacts everything from internal policy to choosing the right software vendors.
Understanding HIPAA: The What of Data Protection
The Health Insurance Portability and Accountability Act (HIPAA) is a federal law passed in 1996. Its core mission is to set a national standard for safeguarding patients' sensitive health information from being shared without their knowledge or consent. In the world of personal injury law, this information is known as Protected Health Information (PHI), and it's the lifeblood of every case you handle.
HIPAA’s requirements are laid out in three key rules:
- The Privacy Rule: This rule dictates how PHI can be used and disclosed. For instance, it’s the reason you must get explicit client authorization before sending their medical records to an expert witness.
- The Security Rule: This one gets technical, setting the standards for protecting electronic PHI (ePHI). It mandates specific administrative, physical, and technical safeguards—think using encrypted email for sending records or ensuring your cloud storage provider has strict access controls.
- The Breach Notification Rule: If a breach involving unsecured PHI occurs, this rule requires you to notify the affected individuals and the Department of Health and Human Services (HHS).
Bottom line: HIPAA compliance isn't a choice. It's a legal mandate for any law firm that handles PHI.
Demystifying SOC 2: The How of Data Management
Unlike HIPAA, SOC 2 isn't a law. A SOC 2 report is an attestation, an official opinion from an independent CPA firm. It evaluates a service organization's controls based on five Trust Services Criteria (TSC) developed by the American Institute of Certified Public Accountants (AICPA).
Essentially, a SOC 2 report is an in-depth, third-party validation of a vendor's security practices. It provides a clear answer to the all-important question: "Can I actually trust this company with my firm’s most sensitive data?"
The five Trust Services Criteria are:
- Security: This is the non-negotiable foundation of every SOC 2 report. It covers all protections against unauthorized access, both digital and physical.
- Availability: This criterion ensures a system is up and running as promised. It’s critical for the case management software your team depends on every single day.
- Processing Integrity: This confirms that a system processes data completely, accurately, and on time. For a legal analytics tool, it means data isn’t being corrupted or altered during use.
- Confidentiality: This focuses on protecting information designated as confidential, like case strategies or settlement negotiations stored in a vendor's system.
- Privacy: This criterion governs how personal information is collected, used, retained, and disposed of, making sure it aligns with the company’s stated privacy policy.
A law firm might be legally required to be HIPAA compliant, but it would look for a SOC 2 report from its software vendors. HIPAA defines the firm's legal duties for PHI, while the SOC 2 report provides confidence that a vendor's operational security is solid enough to handle that data.
A vendor must always include the Security criterion in their SOC 2 audit, but they can choose which of the other four to add. This flexibility lets them tailor the report to their specific services, giving you relevant assurance that they've got their act together. With this foundation, we can now compare HIPAA and SOC 2 in a practical context.
HIPAA vs. SOC 2: Key Distinctions for Your Law Firm
For a personal injury firm, the difference between HIPAA and SOC 2 isn't just a technicality—it directly impacts your legal duties, how you choose vendors, and your entire data security strategy. While both frameworks are designed to protect sensitive information, they come from completely different places and serve very different functions. Getting this right is critical to protecting your clients and your practice.
At its core, HIPAA is a legal mandate, not a choice. It carves out a specific type of data—Protected Health Information (PHI)—and lays down the law on exactly how you must handle it. SOC 2, on the other hand, is a voluntary audit report. It gives a much broader, operational look at a vendor's security systems, assuring you that their internal controls are effective across all sorts of data, not just PHI.
Think of it this way: HIPAA tells you what you are legally required to protect (PHI), while a SOC 2 report proves how a vendor securely manages all of your firm's data.
This is the fundamental distinction. Your law firm is legally bound by HIPAA. The tech vendors you rely on—from case management software to AI-powered medical review platforms—use a SOC 2 report to prove they’re a safe pair of hands for your firm's most sensitive information.
Scope and Focus: A Legal Rulebook vs. a Security Framework
The biggest difference comes down to scope. HIPAA is narrow and deep, with a laser focus on PHI. Its rules are prescriptive, detailing the specific administrative, physical, and technical safeguards you absolutely must have in place to keep patient information confidential, available, and intact. It's built for one industry: healthcare and the businesses that support it.
SOC 2 is broad and flexible by design. It’s structured around five Trust Services Criteria (TSCs) developed by the AICPA: Security, Availability, Processing Integrity, Confidentiality, and Privacy. While the Security criterion is the mandatory foundation, a vendor can choose which other TSCs are relevant to the services they provide you. This makes SOC 2 an industry-agnostic framework that works for any service organization, whether it's a data center or a SaaS provider.
- HIPAA in Practice: Your firm is required to have a formal policy for sanctioning an employee who improperly views a client's medical records. That’s a specific administrative safeguard demanded by the HIPAA Security Rule.
- SOC 2 in Practice: Your case management software provider’s SOC 2 report might cover the Availability criterion. This shows they’ve tested their disaster recovery plans, giving you confidence that you can always access your case files, even if their primary system goes down.
Purpose and Audience: Who Is It Really For?
HIPAA’s purpose is all about regulatory enforcement. The U.S. Department of Health and Human Services (HHS) and its Office for Civil Rights (OCR) are the ones watching. They have the power to investigate complaints and hand out massive fines for non-compliance. The main audience for your HIPAA compliance program is the federal government and, by extension, the clients who trust you with their PHI.
A SOC 2 report has a different job: to build trust and give customers peace of mind. It’s not a government requirement; it’s a response to market demand. Service organizations get SOC 2 audits to prove their security claims are backed by an independent third-party. The audience for a SOC 2 report is your firm's leadership team, your IT staff, and anyone involved in vetting a new technology partner.
The demand for this kind of independent proof has exploded. SOC 2 compliance is now the gold standard for tech platforms handling sensitive data, especially in legal tech. Personal injury firms rely on vendors like Ares to process medical records filled with PHI, making this assurance essential. In fact, SOC 2 adoption jumped by 40% in 2024. While only 7% of startups under $1M in funding have it, that figure climbs to 45% for those over $100M, solidifying its role as a baseline expectation. You can explore more cybersecurity compliance trends and statistics that highlight this industry shift.
A Clear Comparison for Your Firm
To make the distinction crystal clear, the table below breaks down the core differences from the perspective of a personal injury law firm. It shows how each framework applies to your daily operations and your relationships with technology partners.
| Attribute | HIPAA | SOC 2 |
|---|---|---|
| Primary Goal | To legally protect patient health information (PHI) and ensure patient privacy rights. | To provide third-party assurance that a service organization has effective controls over its systems and data. |
| Type | A mandatory U.S. federal law. | A voluntary, market-driven audit framework (attestation). |
| Scope of Data | Narrowly focused on Protected Health Information (PHI). | Broadly covers any client data based on the selected Trust Services Criteria. |
| Who It Applies To | Covered Entities (healthcare providers) and their Business Associates (your law firm, vendors handling PHI). | Any service organization that stores, processes, or transmits client data (e.g., SaaS, cloud providers). |
| Enforcement | U.S. Department of Health and Human Services (HHS); violations can lead to severe fines and penalties. | Market enforcement; lack of a report can result in lost business and client trust. |
| Practical Use Case | Your firm implements HIPAA-compliant procedures for emailing medical records to expert witnesses. | You review a potential vendor's SOC 2 Type II report to verify their security controls before signing a contract. |
Ultimately, understanding these differences allows you to ask the right questions. You don't just ask a vendor if they are "secure"; you ask for their SOC 2 report to prove it, ensuring they meet the high standards required to handle your firm's most critical data.
Choosing Your Compliance Path: HIPAA, SOC 2, or Both?
Deciding between HIPAA, SOC 2, or pursuing both isn't a simple, one-size-fits-all choice. The right path depends entirely on your role within the legal ecosystem, the kind of data you handle every day, and what your clients expect from you. If you get it wrong, you could waste a ton of money on unnecessary audits. Or worse, you could leave critical compliance gaps that expose your firm to steep legal penalties and a damaged reputation.
To cut through the confusion, we'll walk through three distinct scenarios that personal injury firms and their vendors face all the time. This approach will give you a clear framework for figuring out your firm's specific obligations and where you can gain a strategic edge. Once you see how these use cases play out, you can allocate your compliance budget with confidence and build a security posture that actually fits how you work.
Scenario 1: The Personal Injury Firm as a Business Associate
Picture a personal injury law firm that directly requests medical records from hospitals and clinics to build a client’s case. In this situation, the firm isn't just handling sensitive information—it’s acting as a Business Associate under HIPAA. That designation is non-negotiable and leaves zero room for interpretation.
For this firm, HIPAA compliance is a legal requirement, not an option. They are mandated to implement the administrative, physical, and technical safeguards detailed in the HIPAA Security Rule. This means conducting regular risk assessments, training every employee on how to handle Protected Health Information (PHI), and making sure any technology used to store or send client medical records is locked down. Their primary focus has to be on meeting their legal duty to protect PHI.
Scenario 2: The Legal Tech Vendor Serving PI Firms
Now, let's think about a SaaS company that builds AI-powered software to review medical records—a game-changing tool for PI firms. Because this vendor processes PHI on behalf of those law firms, it also qualifies as a Business Associate under HIPAA. As a result, they must be HIPAA compliant and ready to sign a Business Associate Agreement (BAA) without hesitation.
But here’s the thing: HIPAA compliance alone often isn't enough to earn the trust of sharp, security-conscious law firms. These firms need independent, third-party proof that the vendor's entire security infrastructure is solid. This is where SOC 2 comes in. A SOC 2 Type II report delivers that assurance, showing that the vendor's controls for security, availability, and confidentiality have been rigorously tested over a period of time.
For a vendor like this, achieving both HIPAA and SOC 2 compliance is a massive market differentiator. HIPAA checks the legal box, while SOC 2 proves their operational maturity and deep commitment to security. That combination gives law firms the confidence they need to hand over their most sensitive case data.
This flowchart breaks down the decision process, helping you see whether your organization needs HIPAA, SOC 2, or both based on how you handle data.
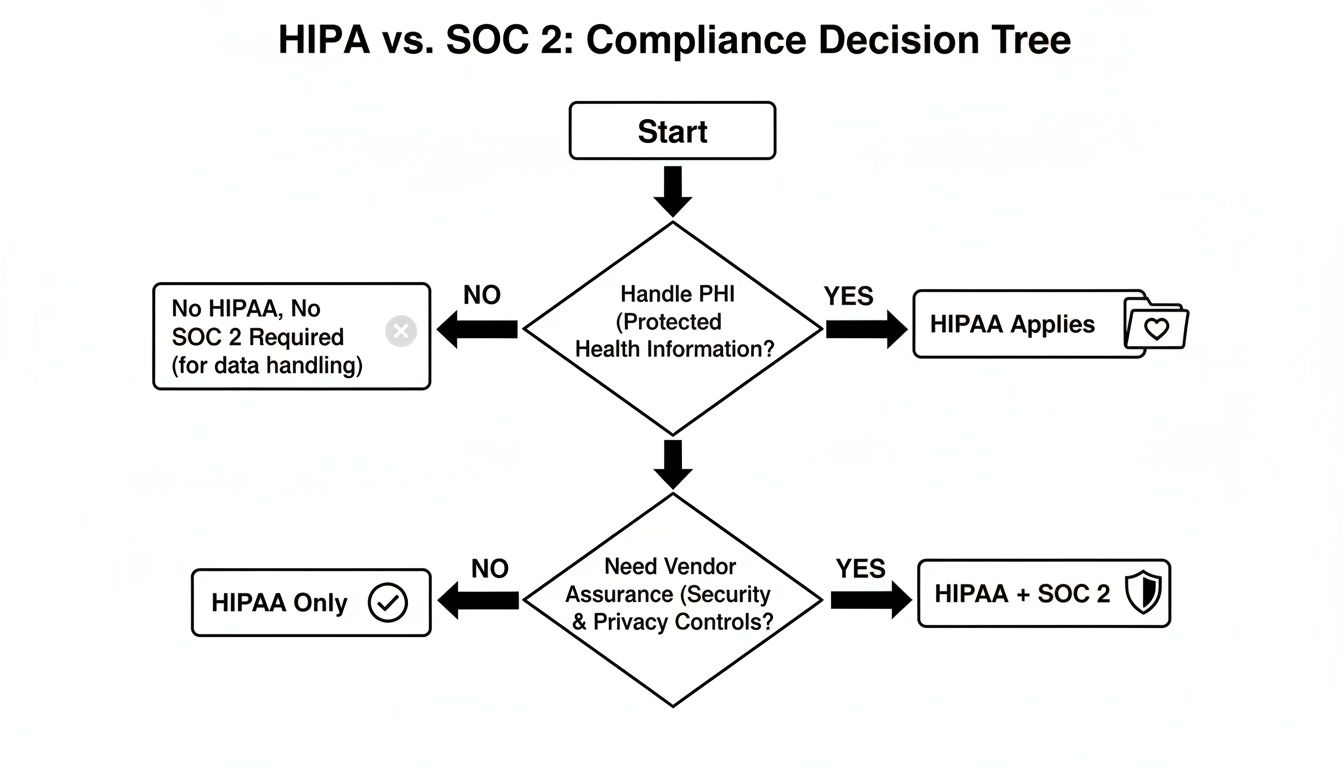
As the visual makes clear, any organization touching PHI must start with HIPAA. The need for SOC 2 is driven by the demand from clients for third-party vendor assurance.
Scenario 3: The Litigation Support Service Without PHI Access
Finally, let's consider a litigation support company providing e-discovery and trial presentation services. They handle incredibly confidential client data—things like case strategy memos and attorney work product—but they never touch PHI. Since there's no protected health information involved, HIPAA is not a legal requirement for them.
Their clients, however, still need absolute certainty that their confidential case files are safe from data breaches or service disruptions. For this type of company, a SOC 2 report focused on the Security and Confidentiality Trust Services Criteria is the main goal. This report acts as definitive proof to their law firm clients that they have robust, effective controls in place to guard all kinds of sensitive, non-medical information.
Key Insight: Melding HIPAA and SOC 2 creates a powerhouse compliance duo for any tech platform in the healthcare-adjacent legal space. As the OCR’s 2024-2025 HIPAA Audit Program targets 50 new entities, the pressure is on. While overlaps in controls like risk assessments and encryption can streamline efforts, challenges remain, with 47% of organizations failing audits multiple times recently. Explore more about these compliance statistics and trends.
By measuring your firm's specific operations against these scenarios, you can map out the most effective path forward. Whether you need the legal shield of HIPAA, the market credibility of SOC 2, or the combined strength of both, a clear strategy is essential for any modern firm. To see how these principles apply in the real world, check out our guide on personal injury case management software and its security implications.
Your Practical Roadmap to Achieving Compliance
Let’s be honest: translating compliance theory into a concrete to-do list can feel overwhelming. But whether you're a personal injury firm tackling HIPAA for the first time or a legal tech vendor pursuing a SOC 2 attestation, a structured approach makes it entirely manageable. This roadmap breaks the journey down into logical phases, starting with a simple, critical question: what data do you have, and where does it live?
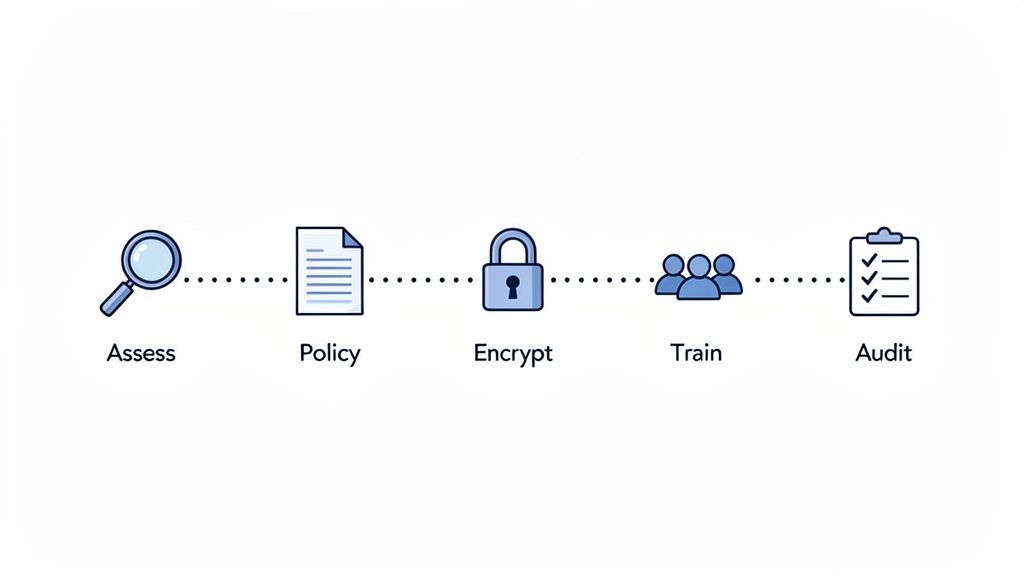
From that starting point, we'll move through creating policies, implementing the right tech, and training your team, all leading up to the formal audit. Think of this as a project plan that a firm’s managing partner or a vendor’s operations manager can pick up and run with.
Phase 1: Foundational Assessment and Planning
You can't protect what you don't know you have. This first phase is all about discovery—laying the strategic groundwork for everything that comes next. It’s the unglamorous but essential part of the process.
- Conduct a Comprehensive Risk Assessment: This is the non-negotiable cornerstone of both HIPAA and SOC 2. You need to systematically look at your operations and identify every potential threat and vulnerability that could compromise your sensitive data, whether it's Protected Health Information (PHI) or other confidential client files.
- Perform Data Mapping: It's time to create an inventory. Map out all the systems, apps, and physical spots where sensitive data is stored, processed, or sent. This means everything from your case management software and email servers to employee laptops and third-party cloud services.
- Define Your Scope: For SOC 2, you have to clearly define which system or service is being audited and select the relevant Trust Services Criteria. For HIPAA, the scope is simpler: if a system or process touches PHI, it's in scope.
Getting this foundational work right prevents you from wasting time and money by focusing your resources where the risk is highest.
Phase 2: Policy and Technical Implementation
With a clear map of your risks and data, it's time to build the guardrails. This phase is about documenting your rules in clear policies and then deploying the technology to enforce them.
First, develop and write down your security policies and procedures. They need to be clear, accessible, and cover everything from acceptable use and access control to what happens during a data breach. For anyone new to this, a practical guide to achieving SOC 2 compliance provides some fantastic insights into the criteria that will shape these documents.
Next, you'll implement the technical safeguards you identified in the risk assessment. Key actions include:
- Enforcing End-to-End Encryption: Make sure data is encrypted both when it’s moving across a network (in transit) and when it’s sitting on a server or hard drive (at rest).
- Implementing Strong Access Controls: Live by the principle of least privilege. This means people should only have access to the absolute minimum data and systems they need to do their jobs. Nothing more.
- Deploying Logging and Monitoring: You need to see what's happening on your network. Set up systems that log user activity and monitor for anything suspicious. This is your early warning system for potential threats. We cover some of these controls in our post on HIPAA compliant document management.
Phase 3: Training and Audit Readiness
Your policies and tech are only as good as the people using them. This final phase is about the human element and getting all your ducks in a row for the formal audit.
An organization's security posture is only as strong as its least aware employee. Continuous training transforms your team from a potential liability into your first line of defense against cyber threats.
Start by rolling out ongoing security awareness training for everyone. This isn’t a one-and-done event. It needs to cover your new policies, how to spot common threats like phishing, and the exact procedures for handling PHI and other sensitive information. Make sure you document who attended and track their understanding—auditors love to see that evidence.
For a SOC 2 audit, the last leg of the journey involves bringing in the experts.
- Engage a CPA Firm: Choose a reputable, independent CPA firm. Critically, make sure they have deep experience with SOC 2 audits in your specific industry.
- Complete a Readiness Assessment: Before the main event, have your chosen firm do a "dry run." This readiness assessment will pinpoint any lingering gaps in your controls so you can fix them before the formal audit begins.
- The Formal Audit (Type 1 and Type 2): The Type 1 audit is a snapshot that assesses the design of your controls at one point in time. The Type 2 audit is the one that really matters to clients; it’s far more rigorous and tests how effectively your controls have been operating over a period of time, usually six to twelve months. This is the report that proves your ongoing commitment to security.
Answering Your Questions About HIPAA and SOC 2
Even when you grasp the basics of these frameworks, real-world questions always pop up, especially in a busy personal injury firm. Let's tackle some of the most common ones to give you a clearer path forward.
Is SOC 2 Compliance the Same as Being HIPAA Compliant?
Not at all. The two are fundamentally different, and it's a critical distinction to make.
HIPAA compliance is a legal requirement dictated by federal law for any organization that handles Protected Health Information (PHI). There’s no getting around it. A SOC 2 report, on the other hand, is a voluntary attestation. It’s the result of an audit by a third-party CPA firm that verifies a vendor’s security controls against the AICPA’s Trust Services Criteria.
Here’s a practical way to think about it: your law firm, as a Business Associate handling medical records, must be HIPAA compliant. To do that securely, you might hire a cloud storage provider. You would require that provider to have a SOC 2 report to prove its security is strong enough for you to trust them with your clients' PHI. One doesn't automatically grant the other.
If Our Firm Is HIPAA Compliant, Do We Need a SOC 2 Report?
For the vast majority of personal injury law firms, the answer is no. Your primary legal duty is HIPAA compliance because you handle PHI. SOC 2 reports are designed for service organizations—think SaaS companies, data centers, or managed IT providers—that need to prove their security to clients like you.
The exception? If your firm has evolved to offer services where you manage or host client data, making you a service organization in your own right. In that case, a SOC 2 report could be a powerful way to stand out and attract larger, more security-focused clients.
Can a Vendor Be SOC 2 Compliant but Not HIPAA Compliant?
Absolutely, and this is a situation you'll see often. A vendor can have an impeccable SOC 2 report that covers Security, Availability, and Confidentiality but still fail to meet the specific requirements of the HIPAA Security Rule.
Their general data controls might be top-notch, but they could be missing HIPAA-specific policies for PHI, have no process for signing Business Associate Agreements (BAAs), or lack the required breach notification procedures.
Always verify both. A SOC 2 report tells you a vendor takes security seriously. But if they're going to handle PHI, you must also confirm their specific HIPAA compliance and, most importantly, get a signed BAA.
How Does This Apply to Disposing of Old Computers or Drives?
Data security doesn’t end when you upgrade your hardware. It extends through the entire lifecycle of your IT assets, and that includes disposal. Simply deleting files from an old computer or server is nowhere near enough to meet HIPAA standards, as PHI can often be recovered with basic tools.
The HIPAA Security Rule explicitly requires you to have formal policies and procedures for the final disposition of electronic PHI and the hardware it’s stored on. This means you have to use methods that render the data completely unrecoverable, such as degaussing magnetic media or physically shredding the drives. For more detail, it's wise to consult expert guidance on IT equipment disposal HIPAA requirements to ensure your process is fully compliant.
What Is the Difference Between a SOC 2 Type 1 and Type 2 Report?
This is one of the most important things to understand when you’re vetting a vendor.
Type 1 Report: Think of this as a snapshot in time. The audit assesses the design of a vendor’s security controls on a specific day to determine if they look good on paper.
Type 2 Report: This is a much deeper, more rigorous audit. It's conducted over a period of time, typically 6-12 months, and tests the operating effectiveness of those controls. It proves they actually work in practice.
A Type 2 report gives you far greater assurance. It demonstrates that a vendor not only designed solid controls but also consistently followed them over an extended period. For any critical system that will handle your firm's sensitive data, you should always insist on seeing a SOC 2 Type 2 report.
At Ares, we understand that navigating compliance is just as important as winning cases. Our AI-powered platform not only automates medical records review and demand letter drafting but is also built on a foundation of enterprise-grade, HIPAA-compliant security. We provide the assurance you need to protect client PHI while dramatically improving your firm's efficiency. Discover how you can save time and strengthen your cases securely at https://areslegal.ai.


