What Is PHI in Healthcare A Guide for Legal Professionals

In the world of personal injury law, we deal with a lot of sensitive information, but none more so than Protected Health Information (PHI). So, what is it, exactly?
Think of PHI as any piece of health data that can be traced back to a specific person. It’s not just the medical diagnosis itself; it's the combination of that health information with something that identifies the individual. This pairing of medical facts and personal identity is what makes the data so sensitive and legally protected.

For a PI firm, every client file—from a doctor's narrative to a hospital bill—is packed with this potent mix. Getting a handle on what constitutes PHI isn't just about good data hygiene; it’s a non-negotiable legal duty under federal law.
The 18 HIPAA Identifiers
The Health Insurance Portability and Accountability Act (HIPAA) is the law of the land here, and it doesn't leave the definition of PHI to guesswork. It gives us a clear list of 18 specific identifiers that officially turn regular health information into protected data. If any of these identifiers are present alongside details about a person's health, care, or payment for care, you're dealing with PHI.
Knowing these identifiers is your first line of defense in building a compliant, secure workflow. Some are obvious, but others can easily be missed.
The U.S. Department of Health & Human Services provides the official list, which we've summarized below.
The 18 HIPAA Identifiers That Create PHI
This table lists the 18 specific data points that, when linked to health information, legally define it as Protected Health Information (PHI) under HIPAA.
| Identifier Category | Specific Examples |
|---|---|
| Basic Demographics | Names, Geographic subdivisions (street, city, county), All dates related to an individual (birth, admission, discharge) |
| Contact Information | Telephone numbers, Fax numbers, Email addresses |
| Government & Financial IDs | Social Security numbers, Medical record numbers, Health plan beneficiary numbers, Account numbers |
| Unique Identifiers | Certificate/license numbers, Vehicle identifiers and serial numbers, Device identifiers and serial numbers |
| Web & Biometric Data | Web Universal Resource Locators (URLs), Internet Protocol (IP) address numbers, Biometric identifiers (finger and voice prints) |
| Visual & Other | Full face photographic images and any comparable images, Any other unique identifying number, characteristic, or code |
The core lesson here is that it only takes one. A single identifier from this list, when combined with health data, triggers HIPAA's strict protection rules. For instance, an email address in the same file as a note about a "broken femur" is enough to create PHI.
Understanding this is fundamental for any legal professional navigating the day-to-day realities of personal injury casework.
The High Stakes of PHI Compliance for Law Firms
Knowing what PHI is is one thing. Understanding the enormous legal and financial risks that come with handling it is another challenge entirely. For a personal injury firm, a single misstep isn't just a theoretical problem—the consequences are severe, swift, and can threaten your firm's reputation and bottom line.
The rules of the road are primarily set by two major pieces of legislation: the Health Insurance Portability and Accountability Act (HIPAA) and the Health Information Technology for Economic and Clinical Health (HITECH) Act. Think of them as the foundation for all PHI protection in the United States.
Your Firm Is a Business Associate
Under HIPAA, any organization that creates, receives, maintains, or sends PHI on behalf of a healthcare provider is called a "business associate." There’s no ambiguity here: personal injury law firms fit this definition perfectly. The moment you request medical records to build a case, you’re on the hook to protect that information just as rigorously as the hospital that created it.
This isn't just a label; it’s a legally binding contract. Being a business associate means your firm must comply with all HIPAA Security and Privacy Rules. This involves putting real administrative, physical, and technical safeguards in place to shield electronic PHI (ePHI) from anyone who shouldn't see it. It’s not optional, and ignoring this duty opens your practice up to serious liability. For a more detailed look at these rules from a legal organization's standpoint, this A Guide to HIPAA Compliance for Legal Nonprofits is a fantastic resource.
The Financial Cost of Non-Compliance
The penalties for HIPAA violations are designed to hurt. The HITECH Act put teeth into enforcement, earmarking around $25 billion to improve health IT and strengthen PHI protection. That funding translates directly to more oversight and much bigger fines.
Civil penalties can climb as high as $50,000 per violation, with an annual limit of $1.5 million for the same recurring offense. Just look at the news from the past decade—major health systems and insurance companies have paid out millions in settlements for mishandling records. The trend toward aggressive enforcement is crystal clear.
These steep fines often stem from surprisingly common mistakes:
- No Risk Analysis: Failing to formally map out where PHI lives in your firm and identify potential security weaknesses.
- Poor Employee Training: Not training your team regularly on HIPAA rules and your firm’s own security policies (and documenting it!).
- Improper Disposal: Tossing paper records into an open recycling bin or forgetting to wipe old hard drives clean.
- Unauthorized Access: A paralegal or attorney looking at a client's records out of curiosity, with no legitimate reason.
A single breach, such as a stolen laptop containing unencrypted client files or an email with PHI sent to the wrong recipient, can trigger a full-scale investigation by the Office for Civil Rights (OCR), the enforcement arm of the Department of Health and Human Services.
Reputational Damage and Lost Trust
Forget the fines for a moment. The damage to your firm’s reputation after a PHI breach can be far worse and longer-lasting. Trust is the currency of the legal profession. Clients share the most intimate details of their medical lives with you, and they expect—rightfully so—that you will keep that information confidential.
A public data breach completely shatters that trust. The fallout is predictable:
- Losing Current Clients: They may no longer feel their sensitive information is safe in your hands.
- Struggling to Attract New Clients: A breach is a public event, making potential clients think twice before hiring you.
- Dealing with Negative Press: Data breaches are newsworthy, and that kind of publicity can stain your firm’s brand for years.
- Getting on Regulators' Radar: Once the OCR knows your name, you can bet you'll face more frequent and intense audits.
Protecting PHI isn't just about checking a compliance box. It’s a core part of being a client advocate and running a smart, sustainable business. The stakes are simply too high to treat it as anything less than a top priority.
Recognizing PHI in Your Daily Casework
The theory behind PHI is one thing, but spotting it in the wild—across a mountain of documents for a single case—is where the rubber really meets the road. For personal injury firms, PHI isn’t some abstract compliance headache; it’s woven into the very fabric of your evidence. Getting this right is fundamental to protecting your clients and your firm from a costly breach.
Just picture a standard case file. You've got narrative medical reports, itemized bills from a dozen providers, X-rays, MRI films, and a long email chain with your medical expert. Every single one of these items is a potential PHI landmine because it connects a person's name to their private medical story.
Common Examples of PHI in a Case File
Every attorney and paralegal needs to develop a gut instinct for what is and isn't PHI. It’s not always obvious. For instance, a quick email from your client describing their back pain, once filed under their name and case number, becomes PHI. A hospital bill detailing procedures from a specific date? That’s PHI, too.
Here are some of the most common forms you’ll see every day:
- Narrative Medical Reports: These are loaded with identifiers—full name, date of birth, medical record number—right alongside detailed diagnoses and prognoses.
- Billing Statements: These documents are a trifecta of PHI, linking your client directly to specific treatments, provider names, and insurance details.
- Diagnostic Images: An MRI or CT scan isn't just a picture. The file's metadata often contains the patient's name, the date of the scan, and the facility's name.
- Expert Witness Communications: Any report or email discussing your client’s specific medical condition for the case is packed with sensitive, identifiable health information.
Manually sorting through these documents is a huge part of building a strong case. If you're looking to make that process faster and more secure, a dedicated medical record review service can add both speed and an extra layer of compliance.
What Is Not Considered PHI
Knowing what isn't PHI is just as critical as knowing what is. This distinction is what keeps you from putting unnecessary locks on data that could be used more freely to build your case. The simple rule is this: if the personal identifiers are gone, it's generally not PHI.
For example, a report on city-wide car accident statistics is not PHI because it's anonymous and aggregated. An internal memo that refers to "the client in the March slip-and-fall case" without using a name or other identifier also falls outside the definition.
The magic word here is identifiability. If a piece of health data can't reasonably be traced back to a specific person, it’s no longer under HIPAA's protective umbrella. This is exactly why proper de-identification is such a powerful tool for legal teams.
To help your team quickly tell the difference, let’s look at some common documents you handle.
PHI vs Non-PHI in a Typical Case File
This table breaks down real-world examples to help your team make faster, more confident decisions when handling case-related documents.
| Document or Data Type | Is It PHI? | Why or Why Not? |
|---|---|---|
| Client’s Hospital Admission Form | Yes | Contains name, date of birth, address, and medical record number linked to a health event. |
| Anonymous Injury Statistics | No | The data is aggregated and does not contain any of the 18 personal identifiers. |
| A Doctor's Deposition Transcript | Yes | Explicitly discusses the patient's medical condition, treatment, and identity for the case record. |
| A Published Medical Journal Article | No | Discusses medical conditions in a general, academic context without reference to specific, identifiable patients. |
Internalizing these distinctions is the first step toward building a compliance-aware culture. When your team can confidently separate sensitive data from general information, you not only protect your client but also operate more efficiently.
Putting Secure PHI Handling into Practice
Knowing what PHI is marks the starting line. But actually building a fortress around your client’s data—and your firm’s reputation—is all about putting that knowledge into practice. This isn't about creating bureaucratic headaches. It's about establishing clear, repeatable workflows that make compliance second nature in your firm's daily operations.
A core concept to get right is the Minimum Necessary Rule. It's a simple idea that requires real discipline: only use, disclose, or request the absolute minimum amount of PHI needed to get the job done. For instance, if you're settling a billing dispute that only needs a patient's account number and date of service, there’s no reason to send their entire medical history.
This discipline starts the moment a document walks through your door (or hits your inbox). You need a system to identify and classify sensitive information right away.
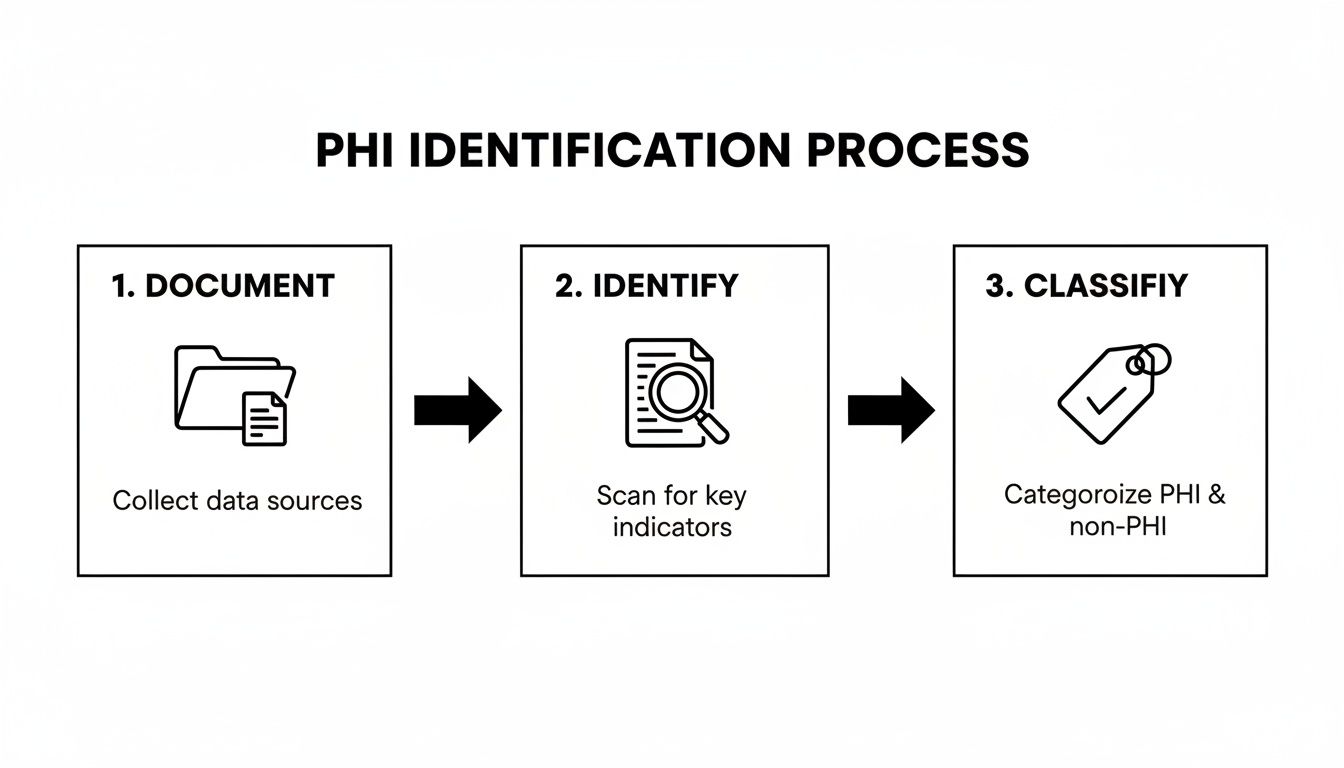
By setting up this kind of initial triage, you ensure documents loaded with PHI are immediately flagged and sent to secure storage, getting the right level of protection from day one.
Building Your Firm’s PHI Security Playbook
A rock-solid security plan is a three-legged stool: technology, policy, and people. Take one away, and the whole thing collapses. Your firm's playbook needs to map out how you handle PHI from the moment you receive it to its final, secure destruction. This means a multi-layered approach that accounts for both digital files and paper records.
For a deep dive into building this strategy, legal professionals should check out this comprehensive law firm data security guide. At a minimum, your plan needs to cover a few key areas.
Key Security Measures:
- Secure Document Transmission: Always use encrypted email or a secure, access-controlled portal to send PHI. Standard email is the digital equivalent of a postcard—it’s a common and completely avoidable source of breaches.
- Access Control Policies: Not everyone in your firm needs to see everything. Implement role-based access so only authorized personnel can view specific client files containing PHI.
- Regular Staff Training: Make HIPAA training mandatory and annual for everyone—attorneys, paralegals, and administrative staff. Documenting who attended and when is your proof of diligence if an auditor ever comes knocking.
- Vendor Due Diligence: Before you share PHI with any third party—whether it's your IT consultant or a record review service—you must have a signed Business Associate Agreement (BAA). This is a non-negotiable legal requirement under HIPAA.
Digital and Physical Storage Best Practices
How you store PHI is every bit as important as how you send it. A misplaced manila folder can cause just as much damage as a hacked server, so your protocols have to be airtight for both.
When it comes to digital files (ePHI), your IT security has to be on point.
- Encryption at Rest: Every computer, server, and external drive holding PHI needs to be encrypted. If a paralegal's laptop gets stolen from their car, encryption is the only thing standing between you and a major data breach.
- Strong Password Policies: Enforce complex passwords and, more importantly, multi-factor authentication (MFA) across all systems that touch client data.
- Secure Network Configuration: Use firewalls and make sure your office Wi-Fi is secure and password-protected. A "guest" network is a great idea, but your main network needs to be locked down.
And don't forget about paper records. They demand their own physical safeguards.
Client files stuffed with paper medical records belong in locked filing cabinets or a secure, access-controlled room. When it's time to dispose of them, they need to be destroyed by a professional, certified shredding service—not just tossed in the blue bin out back.
Creating this secure environment takes deliberate effort. For firms looking for a more structured approach, exploring HIPAA-compliant document management solutions can provide a ready-made framework that ensures you're covering all your bases, both digitally and physically.
Turning PHI from a Burden into a Strategic Asset
For most personal injury firms, managing Protected Health Information (PHI) feels like a purely defensive game. It’s a constant, painstaking effort to sidestep penalties and prevent breaches. But what if that endless stream of sensitive data could be turned from a compliance headache into a genuine strategic advantage? With the right HIPAA-compliant technology, that shift is already happening, and it’s changing how firms build their cases from the ground up.
Anyone who's worked a PI case knows the traditional process is a grind. Paralegals and attorneys spend untold hours wading through thousands of pages of unstructured medical records, trying to manually piece together a coherent story. This work isn’t just slow; it’s a minefield for human error, where one missed detail can gut the strength of your case.
This is exactly the problem AI-powered platforms were built to solve. By securely automating the review of medical records, these tools can organize a chaotic flood of PHI into a clear, strategic asset. And that’s where truly understanding what is PHI in healthcare gives your firm a serious competitive edge.
From Unstructured Data to Actionable Intelligence
Think about a standard personal injury case. Your client has seen multiple specialists, gone through various treatments, and left a mountain of paperwork in their wake. Manually digging through all of it to find the "golden nuggets" of evidence is an exhausting, monumental task.
AI completely changes that equation. A HIPAA-compliant platform like Ares can take in thousands of pages of PHI and pull out the most critical data points in minutes.
Key Data Extracted by AI:
- Diagnoses and Conditions: Instantly flags every single diagnosis mentioned across all provider notes.
- Treatment Timelines: Automatically constructs a clean, chronological list of every procedure, therapy session, and prescription.
- Billing and Costs: Extracts and adds up all medical expenses, helping you build a precise damages model.
- Provider Information: Organizes the entire case by every doctor, clinic, and hospital involved.
This process essentially transforms a messy pile of documents into a structured, searchable database for each case. The end result is a powerful, high-level summary that gives your legal team an almost instant grasp of the essential facts.
This shift does more than just save time—it fundamentally improves the quality of your case preparation. By automating the grunt work, attorneys can finally focus on high-value tasks like strategy, negotiation, and client communication.
The Strategic Impact of Automated PHI Analysis
The ripple effects of using technology to handle PHI go far beyond simple efficiency. It positively impacts your entire firm, from your total caseload capacity to the outcomes you secure for clients. When you stop treating PHI as a mere liability, you unlock its true potential to fortify your arguments.
In the personal injury world, PHI is the core evidence for damages. A single moderate case can easily generate hundreds or even thousands of pages of records from 5–20 different providers. Platforms like Ares add immense value by converting this sprawling PHI into structured timelines, condition summaries, and demand-ready narratives, all while maintaining strict HIPAA-compliant controls like electronic PHI encryption, role-based access, and detailed audit trails. When firms eliminate 10+ hours of manual review per case, they not only boost their margins and capacity but also reduce the human handling of sensitive data, which statistically lowers the risk of unauthorized access or an accidental disclosure. You can find more insights on secure data handling in this comprehensive guide to protected health information.
Strengthening Security and Minimizing Risk
One of the biggest wins of using a dedicated, HIPAA-compliant platform is the security that’s baked right in. Every manual touchpoint—every email, every printout, every transfer to a personal drive—is another opportunity for a data breach. Automating the review process inside a secure, closed-loop system slashes these exposure points dramatically.
Security benefits include:
- Reduced Human Handling: The less PHI is manually passed around, copied, or moved, the lower your risk of an accidental leak.
- Centralized Control: All PHI for a case lives in one secure, encrypted place instead of being scattered across vulnerable desktops and inboxes.
- Enhanced Audit Trails: Modern platforms automatically log every single action, giving you a clear record of who accessed what data and when—a critical component for compliance.
By embracing technology designed for the specific challenges of personal injury law, firms can do more than just manage PHI—they can master it. This strategic approach turns a compliance burden into a wellspring of efficiency, accuracy, and security, ultimately helping you build stronger cases and achieve better outcomes for your clients.
Choosing the Right HIPAA-Compliant Technology Partner
For a modern law firm, picking a technology partner is a huge decision. When you're handling client data that includes PHI, the stakes shoot through the roof. The right partner becomes a digital fortress for your clients' most personal information; the wrong one can easily become your biggest liability.
Vetting potential vendors isn't about falling for a slick sales pitch. It requires a sharp eye for specific, non-negotiable security features. True HIPAA compliance is built from the ground up with strong technical and administrative safeguards. You have to ask the tough questions and demand proof of a vendor’s security before handing over a single piece of client PHI.
Core Features of a Compliant Platform
When you’re looking at any platform that will touch PHI, a few features are absolute must-haves. Think of them as the price of admission. If a vendor can't confidently show you these, it's an immediate red flag.
Your evaluation checklist must include:
- End-to-End Encryption: Data has to be locked down at all times—while it's being uploaded, sitting in storage, and moving between systems. If it’s ever intercepted, encryption ensures it's just unreadable gibberish.
- Detailed Audit Logs: Who accessed what, and when? The platform must keep a clear, unchangeable record of every action. This isn't just a "nice-to-have"; it's a core HIPAA requirement and your first line of defense in an audit.
- Strict Access Controls: You need fine-grained control over who sees what. Attorneys and paralegals should only be able to access the PHI necessary for their specific cases, and nothing more.
Beyond the technology itself, there’s a critical legal document: the Business Associate Agreement (BAA). This is a contract where the vendor legally promises to protect PHI according to HIPAA's rules. If a vendor won't sign a BAA? Walk away. It’s the clearest sign they aren’t equipped to handle sensitive health information.
Vetting a Vendor: A Practical Example
So, what does an enterprise-grade, HIPAA-compliant platform actually look like in the wild? Take a tool like Ares, which was built specifically for the high-stakes world of personal injury law, where nearly every document is saturated with PHI.
A trustworthy partner won't hide their security infrastructure. They'll be transparent about it.
The key takeaway here is transparency. A partner you can trust will openly detail their security measures, from their data encryption standards to their secure development process. This is what gives you confidence that your data is actually protected.
By choosing a partner with this level of security baked in, you’re doing more than just adopting a new piece of software. You're strengthening your firm's commitment to protecting your clients. This forward-thinking approach is vital when choosing the best case management software for law firms that will become the operational heart of your practice.
Ultimately, your technology partner should be more than just a software provider—they should be an extension of your firm's own security and compliance program.
Making a strategic decision to partner with a vendor that both improves your efficiency and acts as a secure vault for client data is a win-win. It protects your clients, defends your firm’s reputation, and builds a solid foundation for growth.
Frequently Asked Questions About PHI
Even when you feel you've got a handle on PHI, the real world has a way of throwing curveballs. Inevitably, specific questions pop up during casework that can leave you second-guessing. Here are a few common situations legal professionals run into, along with some clear answers to help you navigate those gray areas and stay compliant.
Does Redacting a Client's Name De-Identify the Record?
Not on its own, no. Taking out a client's name is a good start, but it's rarely enough to completely de-identify a document. Think about it: if a medical record still has a unique ID number, specific treatment dates, and details about a rare diagnosis, it might not be too hard to connect the dots back to a single person.
To achieve true de-identification under the HIPAA Safe Harbor method, you have to scrub all 18 specific identifiers. So, for your firm's purposes, it's always smartest to treat any client medical document as PHI unless you know for a fact it's gone through a formal, complete de-identification process.
Can We Just Use Our Standard Cloud Storage for PHI?
Using the personal or standard version of cloud storage services like Google Drive or Dropbox for case files containing PHI is a huge gamble and a major compliance risk. These basic accounts just aren't built with the security architecture and legal guarantees that HIPAA demands.
That said, many providers offer business-tier solutions, like Google Workspace or Dropbox for Business, that can be configured for HIPAA compliance. But it’s not automatic. Your firm would need to activate specific security features, lock down access controls, and—most critically—sign a Business Associate Agreement (BAA) with the provider before a single byte of PHI is uploaded.
A Business Associate Agreement (BAA) is a formal, legally required contract under HIPAA. It's signed between a covered entity (or another business associate, like your firm) and any vendor that will handle PHI on its behalf. This document legally binds the vendor to uphold the same strict security and privacy standards that apply to you.
Why Is a Business Associate Agreement So Important?
Think of a BAA as the legal foundation of your relationship with any outside vendor that touches client PHI. It's what contractually obligates your partners—whether it’s your IT consultant, a document shredding service, or a medical record review platform—to protect that data just as rigorously as HIPAA requires you to.
Without a BAA in place, you’re effectively sharing sensitive health information without the necessary legal safeguards. This puts your firm in immediate violation of HIPAA. It's a non-negotiable step that must be completed before you share any client health information. Getting this right is fundamental to building a secure, compliant practice.
Managing PHI securely is a must, but it doesn't have to be a manual, time-draining process. Ares offers an AI-powered, HIPAA-compliant platform designed to automate medical record review. It can turn thousands of pages into clear, case-ready insights while ensuring your client's data stays protected. Find out how you can save over 10 hours per case and reinforce your security at https://areslegal.ai.


